Hi guys ! I will show you writeup Re1 in WhiteHat Contest 11
You can download in here
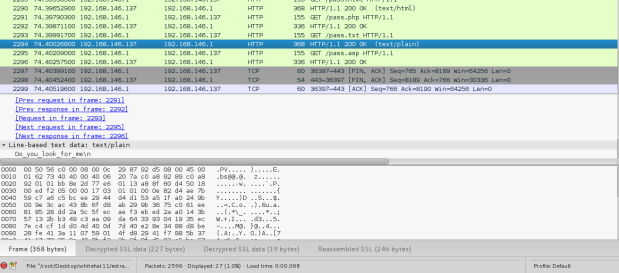
We have file ELF64. Load it into IDA Pro64bit and view source we can get Main function
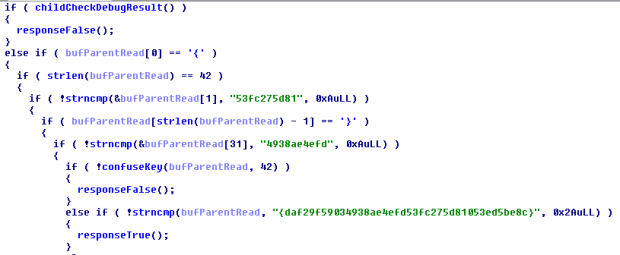
Then, program is compare with 1 string have first character is “{“, have long 42 bits, next 10 characters is “53fc275d81”, last previous is “4938ae4efd” and last characters is “}”. After, program call Confusekey funtion
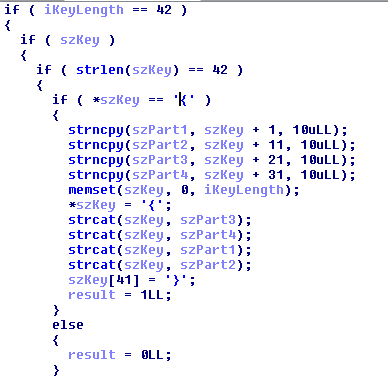
In Confusekey function, it is responsible for changing the order of the blocks. First string have 42 bits, skip first and last character then we have 40 characters, divide into 4 blocks, each block have 10 characters. We recived :
Block 1 = Block 3
Block 2 = Block 4
Block 3 = Block 1
Block 4 = Block 2
Then, we have new string is ‘{‘+Block3+Block4+Block1+Block2+’}’
Return main function we will get first string of Confusekey to compare with string {daf29f59034938ae4efd53fc275d81053ed5be8c}.
So we infer search string is {53fc275d81053ed5be8cdaf29f59034938ae4efd}
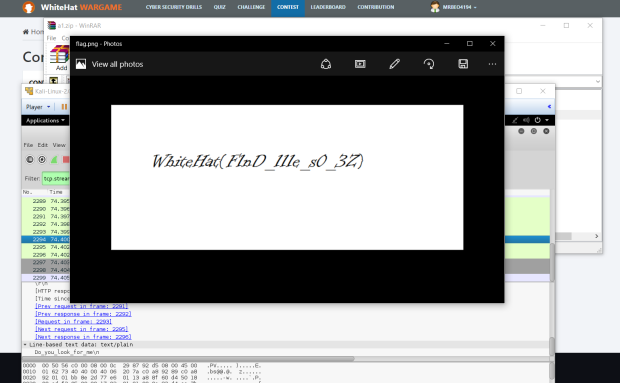
Flag = {53fc275d81053ed5be8cdaf29f59034938ae4efd}