Hi guys! today i will show you how to solved Forensic 100 – TMCTF.
Download file from here and open by wireshark.
you can see it to be encryption by WEP was included as the component of the original privacy IEEE 802.11.
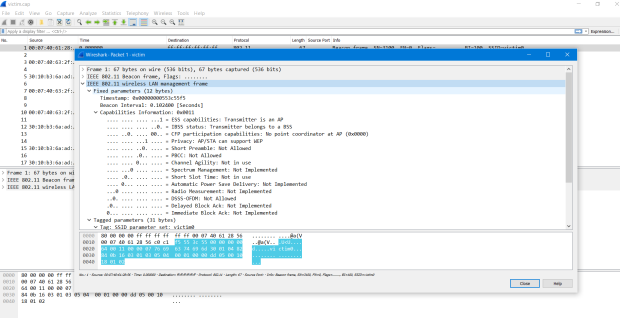
The attacker was wiretapping and find ways cracking them.
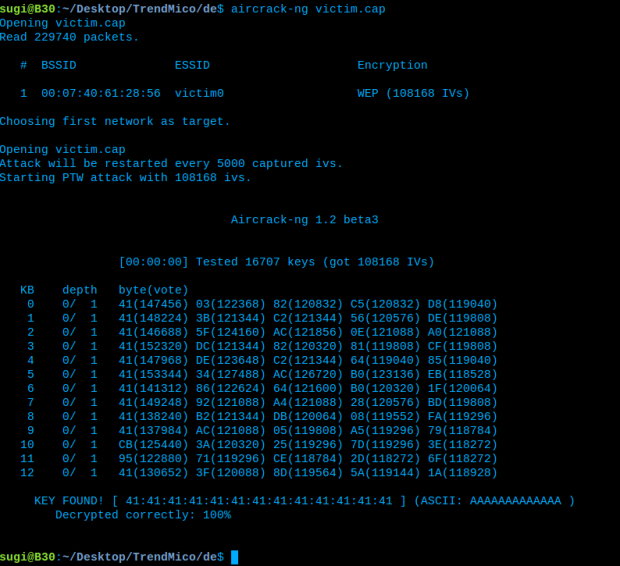
First, we will look for an crack password file pcap.
Use aircrack-ng tool is popular, i try that.
The next step, we will decrypt the file from password we just got.
Use Airdecap-ng to decrypt victim.pcap
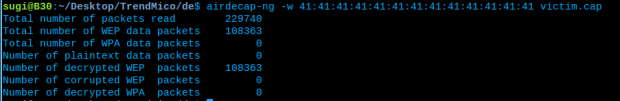
So we can got file victim-dec.pcap
Then, we must find the ip of the sender and the receiver to filter the essential information. In pcap file information has a lot of garbage, so pcap file made will heavier and more complex.
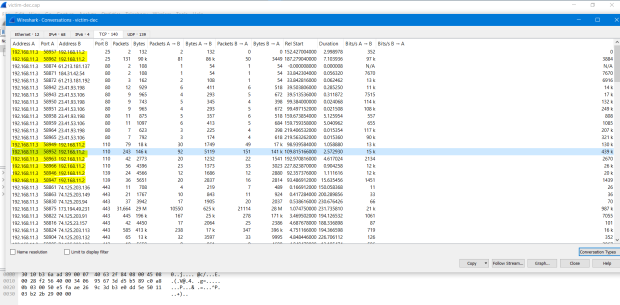
Try filter some port don’t be encrypt and focus to ip 192.168.11.3 and ip 192.168.11.2.
Follow it, we will see what we need
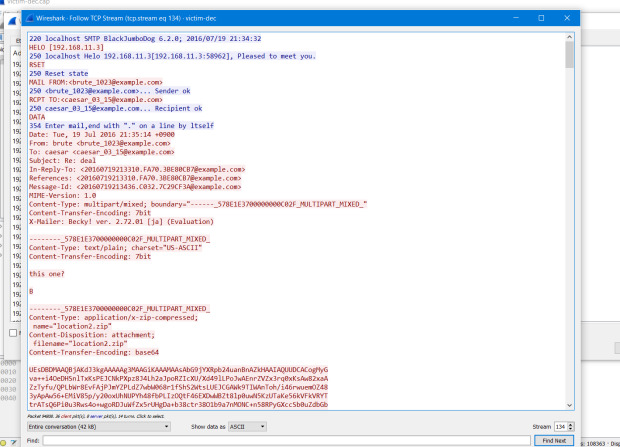
Short conversation, and decode base64 to get file location2.zip.
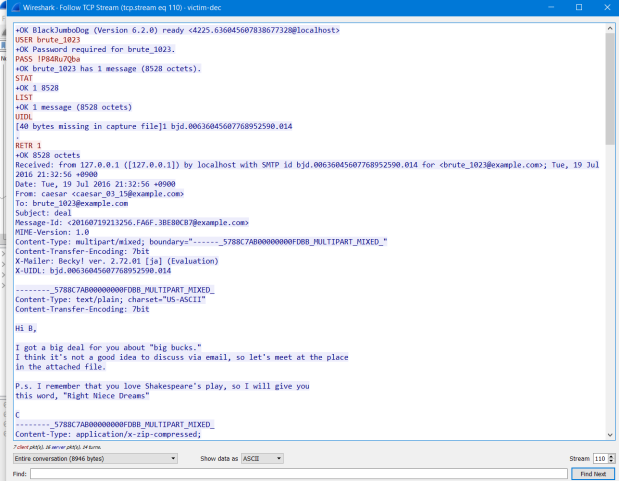
We will find words “Right Niece Dreams” and hint from admin is “Et tu Brute, Then FALL C,A,E,S,A,R” ,so password is “miDNight” and get secret location.
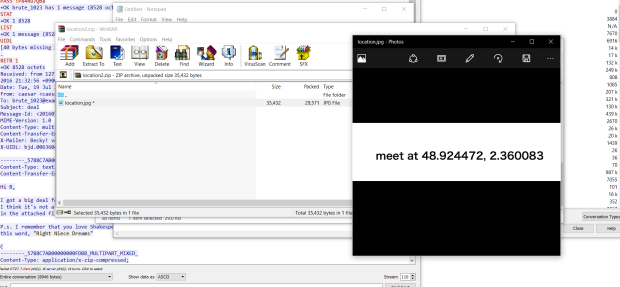
And use gps-coodinates.net to get location we need.
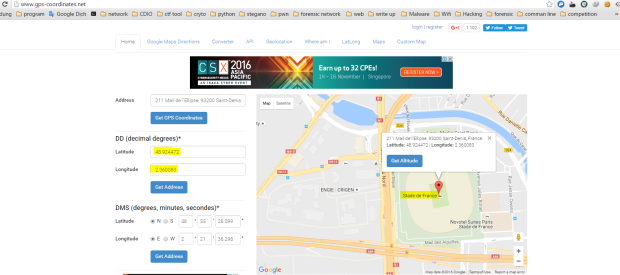
TMCTF{Stade de France} :))